System Requirements
The TechWolf Skill Sync integration will make use of existing Workday functionality. The customer will need a TechWolf contract with a live TechWolf tenant. This TechWolf tenant must be populated with (a subset of) the worker’s entities in Workday.Workday Configuration
A Workday integration user must be configured in the Workday tenant with an implementation security group.If you already have a Job Skill Sync integration configured, you can either
set up a new, separate configuration or reuse parts of the existing one.
When reusing the existing setup, the same ISU can be kept, with only the
Permissions needing to be updated in step 4. Additionally, when using OAuth,
the API Client scopes also need to be updated in step 6.
Authentication
The integration supports both OAuth and Basic Authentication. For enhanced security, we recommend using OAuth authentication. To set up OAuth, you must complete all configuration steps (including Basic Authentication and OAuth setup). If you already have Basic Authentication configured, or prefer to continue using it, we will continue to support this method as well. What you’ll share with TechWolf: If you choose Basic Authentication:- Workday API URL
- Username
- Password
- Workday API URL
- Token URL
- Client ID
- Client secret
- Refresh token
Basic Authentication Setup
-
Create Integration System User (ISU)
Create Integration System Userbusiness process.- Do not allow UI sessions as this user will only be used for automations.
- Please securely store the username and password of this user.
-
Update password expiration rules for ISU
- In the
Maintain Password Rulesbusiness process under “System Users exempt from password expiration” add the newly created ISU to the list. - Note: This ensures the integrations will keep running without interruptions due to password expiration.
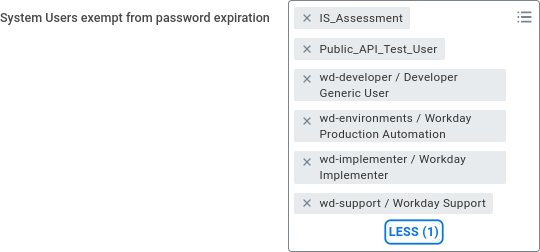
- In the
-
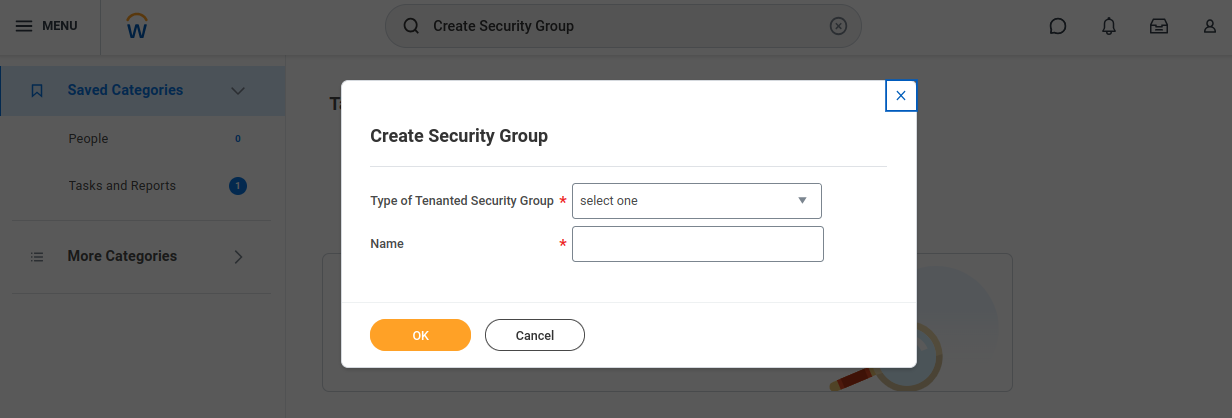
Set up security permissions for the ISU through security policies
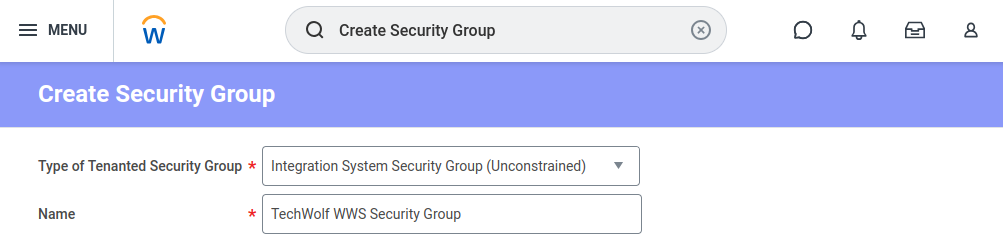
- Go to
Create Security Group, choose “Integration System Security Group (Unconstrained)”. - Note on acceptance testing: Consider using two different security groups, one Unconstrained and one Constrained. This way, the test-set is scoped while the correct permissions are applied for other Web Services.
- The next screen presents you with an Edit form to add additional information. Add your ISU to the list. This can be changed later too. Do not check “Inactive”.
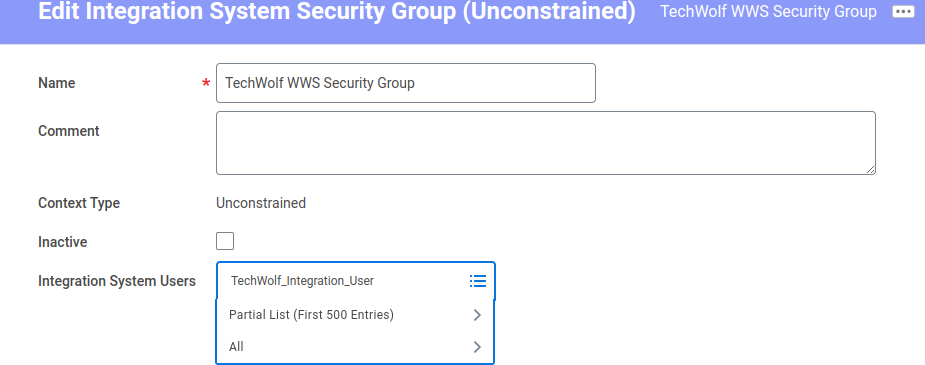
- Go to
-
Edit the Security Group’s domain security policies
- Search for “View Security Group” and select your created security group.
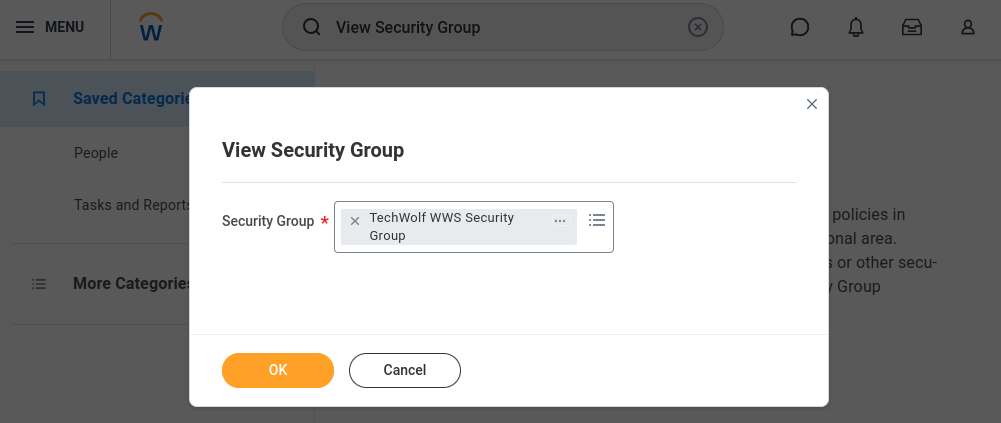
- Select the option menu next to the Security Group’s name, go to “Security
Group” and select “Maintain Domain Permissions for Security Group”.
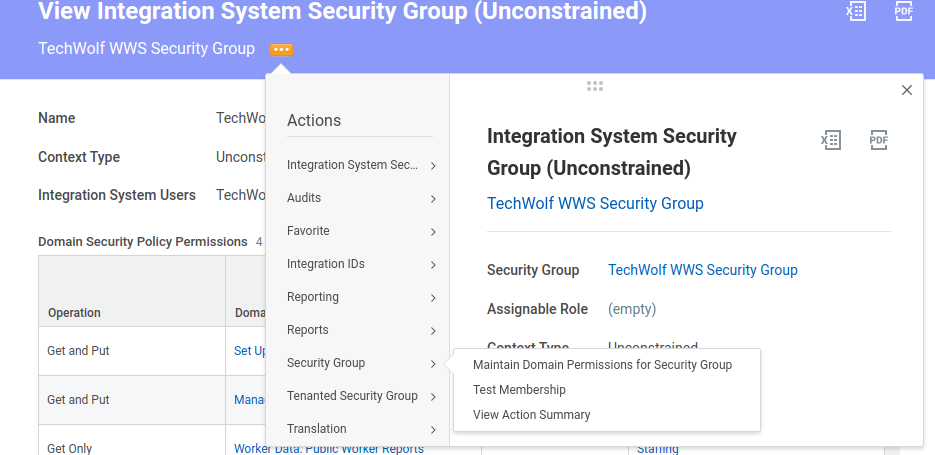
- Under Integration Permissions add the following Domain Security Policies,
and run the
Activate Pending Security Policy Changestask to apply the changes.
Domain Security Policy Access Manage: External Skills Put Person Data: Skills Put Set up: Skills and Experience Put - Search for “View Security Group” and select your created security group.
-
Find out the correct Workday API URL
- Search for
Public Web Servicesin the search bar at the top of the Workday home page. - In the list, click the three dots next to the
Human Resources (public)entry. selectView WSDLunderWeb Service.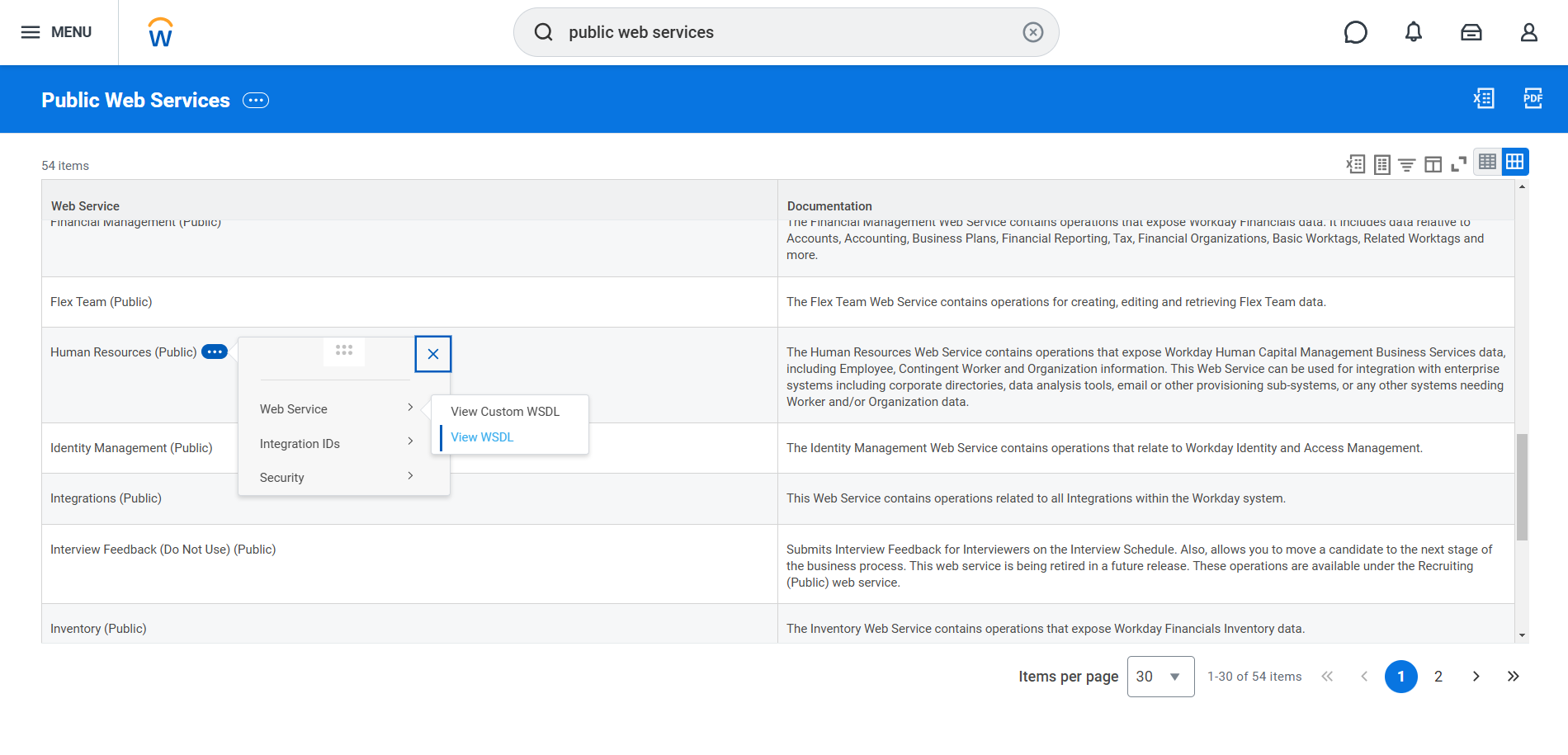
- The resulting page will take some time to load. Once it is loaded, look for
“soapbind:address location” near the bottom of the page. You will see a section like this:
- Copy the base tenant URL up to and including your tenant name. The service name and version should be excluded from the URL.
- Note that the API URL can differ between implementation tenants and production tenants, so the steps described above need to be repeated for each tenant individually.
- Search for
OAuth Authentication Setup
OAuth users must complete the Basic Authentication steps above first, then
follow these additional OAuth-specific steps.
-
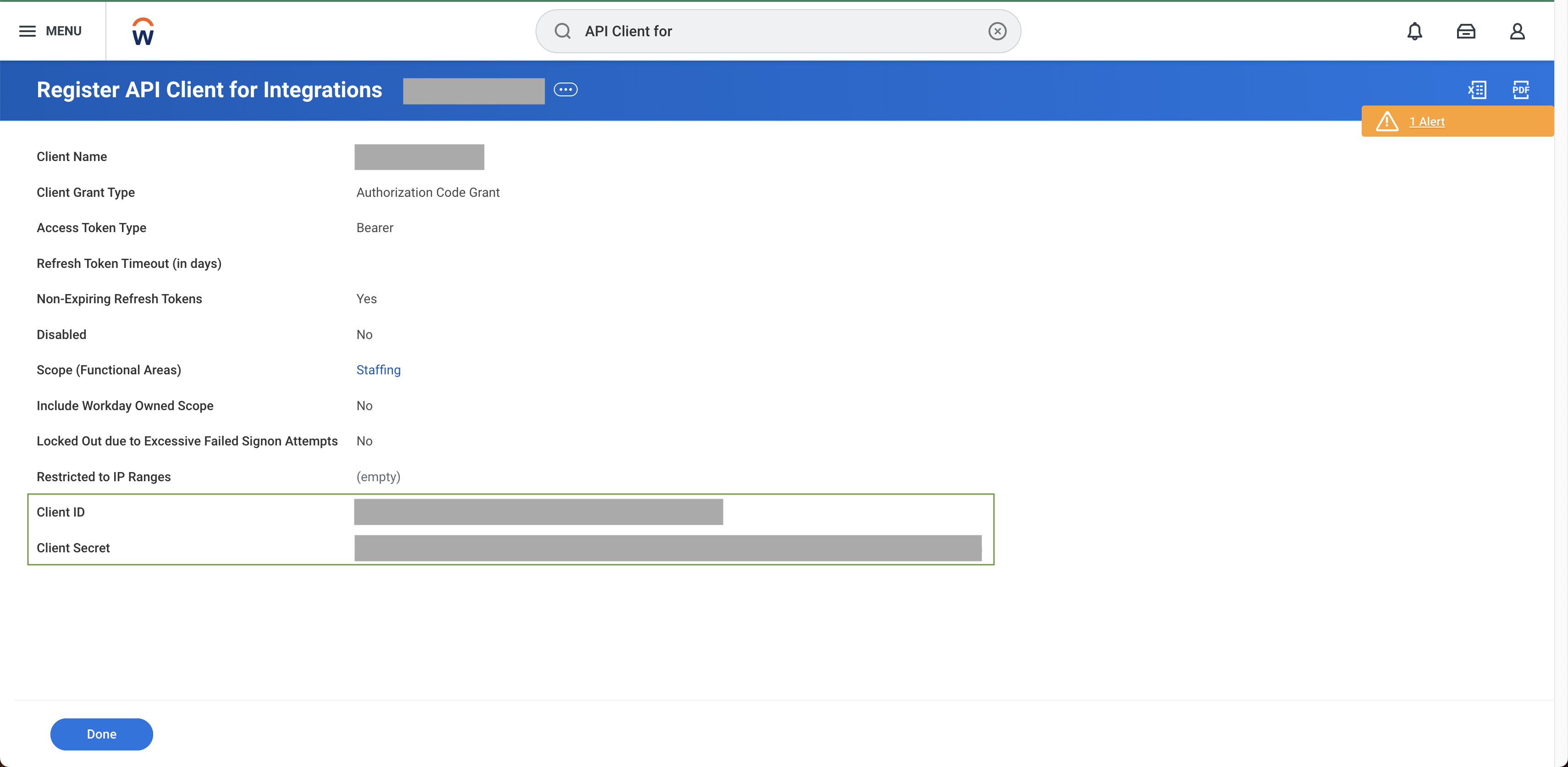
Create API Client for Integrations
- Search for “Register API Client for Integrations” business process
- Enable non-expiring refresh tokens to ensure continuity of service
- Add the appropriate scopes:
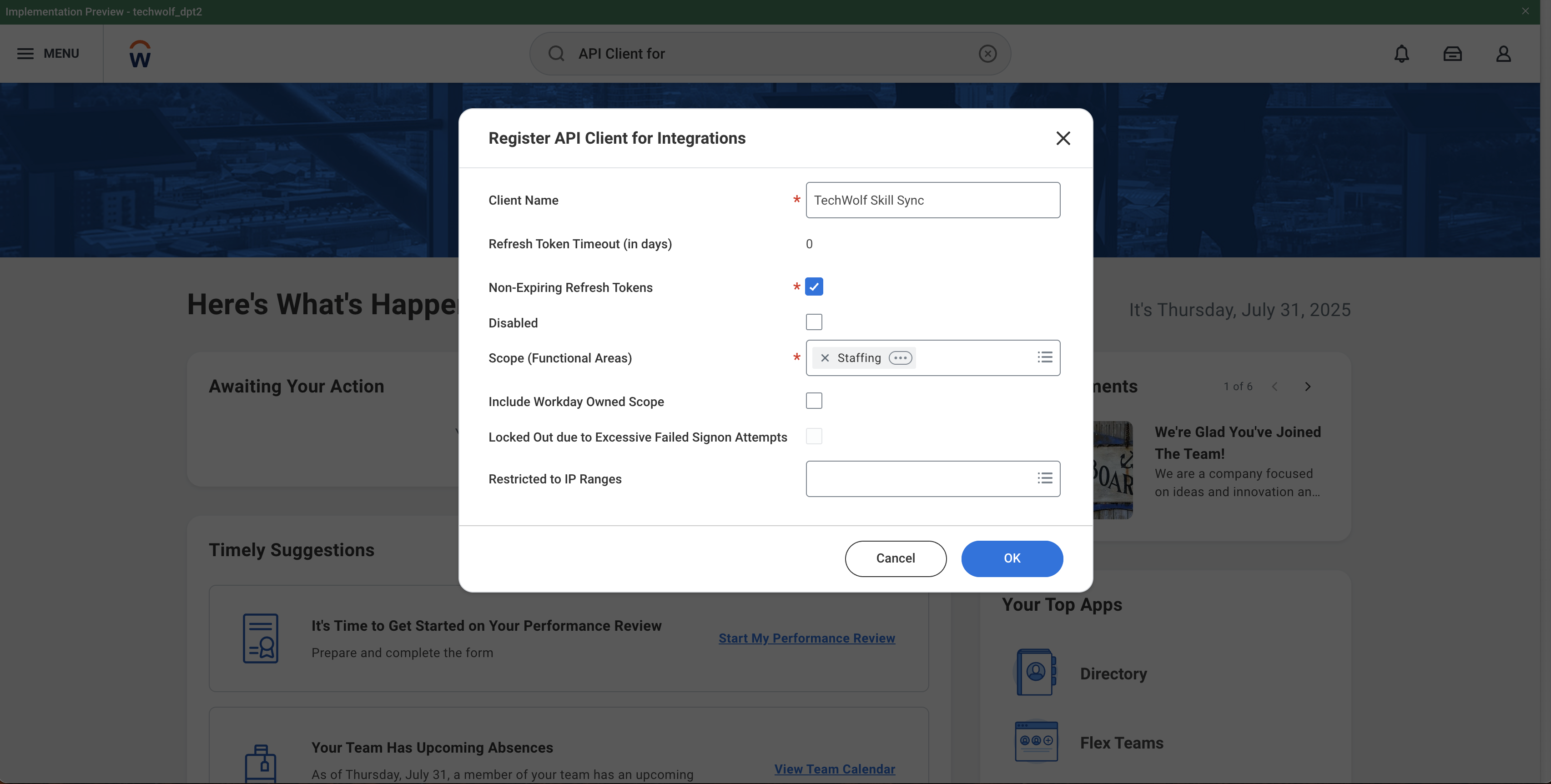
- Securely store the client ID and client secret
-
Generate Refresh Token
- Search for “View API Clients” report
- Click “API Clients for Integrations” tab
- Note down the token endpoint. You will need to share this later.
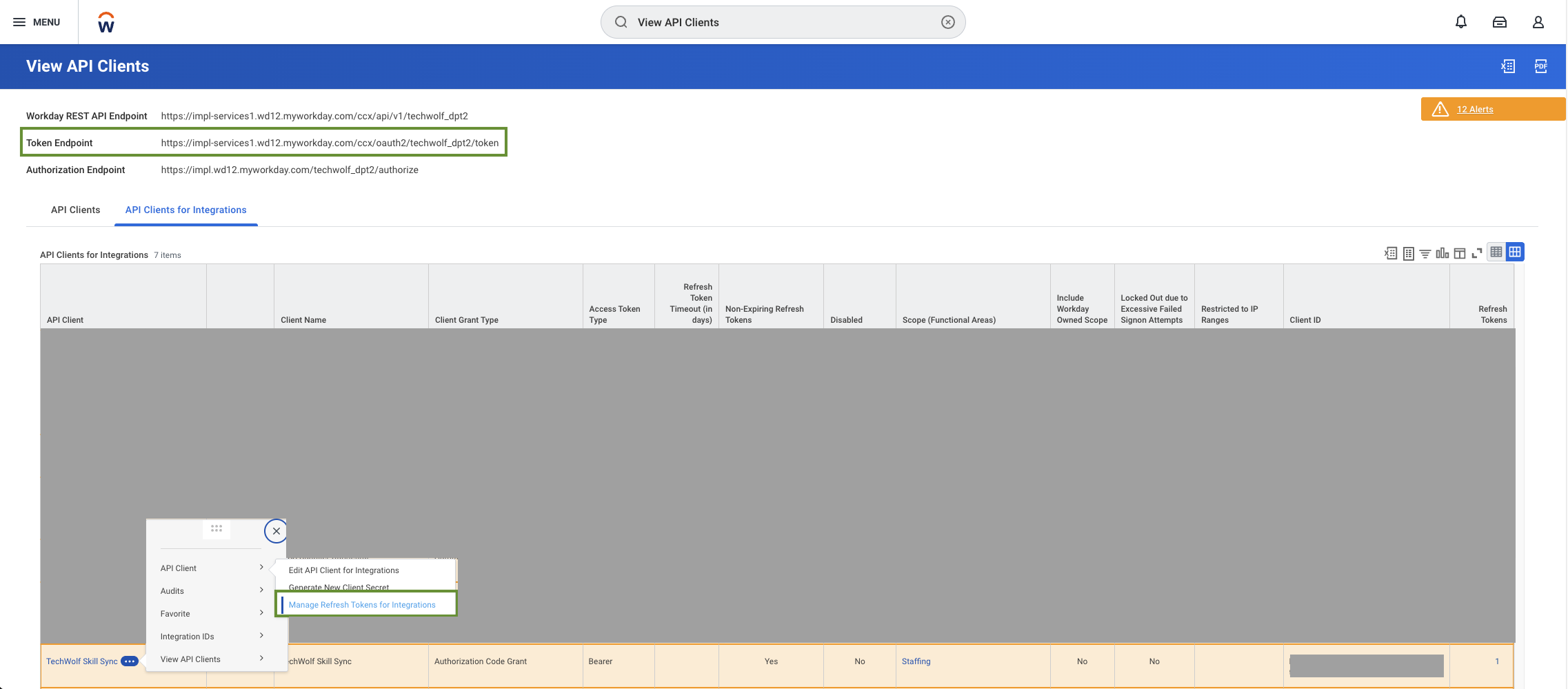
- Find your API client and select “Manage Refresh Tokens for Integrations”
- Under “Workday Account”, type in your ISU
- Press OK
- Check the box “Generate new refresh token”
- Press OK
- Securely store the refresh token.
TechWolf Configuration
Handled by TechWolf.Linking Workday & TechWolf
This section is only required if the customer is NOT using the Workday ID as the API ID in TechWolf.Seamless Matching of Employee IDs
A critical aspect of this process is the seamless coupling of Employee IDs across both platforms. There are two options for direct ID matching:-
Using Employee IDs: If you want to use Workday Employee IDs as the
identifier field in Workday, then this same ID must also be used as the
Employee
external_idin TechWolf. -
Using Workday IDs (WIDs): If you want to use Workday IDs as the
identifier field in Workday, then this same ID must also be used as the
Employee
external_idin TechWolf.
Creating Custom Properties
- For each Employee in the TechWolf system, introduce a new custom property such
as
employee_workday_id. This property will store the corresponding Workday ID of the Employee. - Detailed instructions for creating new custom property definitions can be found here .
Setting Custom Property Values
- Once the custom property is defined, assign the Workday ID to each Employee’s TechWolf profile.
- Steps for setting these values are outlined here .
Deployment Methodology
The following tasks and responsibilities assume that:- The customer has the appropriate TechWolf API license(s).
- The TechWolf API contains all Employee information corresponding to Workday workers and data from other external systems.
- A Skill Profile validation tool (e.g., MS Teams bot) is set up and configured (see separate deployment guide).
Deployment Tasks & Responsibilities
- TechWolf: Setup Skill Sync environment and tenant requirements
- Customer: Create Integration System User (ISU) based on workflow described above.
- Customer: Choose and configure authentication method (Basic or OAuth).
- Customer: Share authentication credentials with TechWolf:
- For Basic Authentication: ISU username and password
- For OAuth Authentication: client ID, client secret, and refresh token
- Customer: Share Workday API URL with TechWolf.
- TechWolf: Run initial sync of worker profiles with TechWolf API.
- TechWolf: Setup tenant configuration and start bidirectional sync process.
- Customer: Check end-user test scenarios.