Required Roles for Teams Installation
The required roles for the Teams installation are:- Azure Admin: A user with administrative privileges who can grant permissions to the Skill Assistant app and run a script to force install the app for users.
- Teams Admin: A user with administrative privileges who can install and manage apps in Teams.
- Azure Group Admin: A user that can create and maintain an Azure group of users.
- Customer Contact with TechWolf: A designated representative who coordinates with TechWolf’s team to facilitate the integration process, provide necessary information, and ensure successful implementation of the Skill Assistant in your Teams environment.
Required Teams App Permissions
The Skill Assistant application requires the following permissions:User.Read.Allapplication permissionUser.Readdelegated permission
User.Read.All application permission allows the app to read user profiles
for all users in the organization. This is necessary for the Skill Assistant to
fetch the Employee ID of a user using the Microsoft Graph API. More information
about this can be found in the
Linking Microsoft Teams users and employee profiles in TechWolf
section. The User.Read.All permission is also required for the Skill Assistant
to fetch the user’s country information, which is used to send suggestions
according to the user’s country timezone when the user-based scheduling setting
is enabled. This country information is read from the usageLocation property
in Microsoft Graph.
For the Skill Assistant to use user timezones (when user-based
scheduling is enabled), the usageLocation property must be set for each
user in Microsoft 365 / Entra ID. The Skill Assistant uses usageLocation to
derive the user’s timezone. If usageLocation is not set for a user, that
user will receive suggestions according to the tenant’s default timezone
instead. You can set usageLocation in the Microsoft 365 admin
center or via Microsoft
Graph. The Skill
Assistant also updates a user’s timezone whenever it receives it from Teams
(e.g. from the message context); this only happens after the user has sent
their first message to the Skill Assistant.
User.Read delegated permission allows the app to read user profiles for
the user who is currently logged in. This is necessary for the Skill Assistant
to properly show the Skill Profile Tab.
Installation steps
The installation consists of several steps, which are described in detail below. TechWolf needs to configure the Skill Assistant to work with your tenant, you need to give the app the right permissions, and you need to install the app in your Teams environment.Share your Azure Tenant ID with TechWolf.
Share your Azure Tenant ID with TechWolf. TechWolf will configure
the Skill Assistant to work with your production tenant. Follow the
steps in Get Azure Tenant
ID
to find your Azure Tenant ID.
Link Microsoft users to employee profiles in TechWolf
We need a method to link employee profiles in the TechWolf API to Teams
Users in Microsoft Teams. See Linking Microsoft Teams users and
employee profiles in TechWolf
.
Whitelist the Skill Profile Tab URL (if required)
If your organization restricts outbound internet traffic by default
(i.e., blocks all URLs unless explicitly allowed), you will need to
whitelist the following URL to ensure the Skill Profile tab functions
correctly:
teams-tab-frontdoor.skillengine.eu. This URL doesn’t handle
any personal or company data, it only loads the visual interface for the
Skill Profile tab in Microsoft Teams.Grant permissions to the Skill Assistant app
Grant the app the required permissions. Follow these
steps.
Customize the branding of the Skill Assistant app
Customize the branding of the Skill Assistant app by following these
steps.
Install the Skill Assistant for users
Install the Skill Assistant for users following these
steps
Linking Microsoft Teams users and employee profiles in TechWolf
In order for TechWolf’s Skill Assistant to deliver personalized and timely skill suggestions via Microsoft Teams, it is crucial that we can accurately link each employee in your organization to their corresponding Teams user. There are two options to link the two IDs: If this is set up correctly, the TechWolf Skill Assistant will be able to fetch all skill suggestions and send them to the right Teams user.Through Microsoft Graph (preferred)
The preferred method is to use the Microsoft Graph API to fetch theEmployee ID property for each user. This requires the Employee ID property
to be set in Azure for each user, and for that Employee ID property to exactly
match the employee ID known within TechWolf’s SkillEngine API. In that case we
can automatically link the Teams user to the employee profile in TechWolf.
Ideally, the Employee ID is filled in automatically using an integration with
your organization’s HR system. If this is not possible, you can manually
populate the Employee ID property by following this guide:
Set Employee ID in Microsoft 365
Through Custom Properties
If theEmployee ID property is not set in Azure, or if the Employee ID
property in Azure is different from the employee ID stored in the TechWolf
SkillEngine API, we can use a
Custom Property
for each employee profile in the TechWolf SkillEngine API. The Azure ID should
be stored in the Custom Property with the key employee_azure_id. The mapping
between the employee ID known in TechWolf’s SkillEngine and their corresponding
custom property should be send to TechWolf via the datasource integration so
that we can store it accordingly.
The Azure ID we require (often referred to as the Object ID) has the
following format:
xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx (e.g.
3f2a9c4e-7b6d-4e2b-9c9a-1a2b3c4d5e6f).Grant permissions to the Skill Assistant app
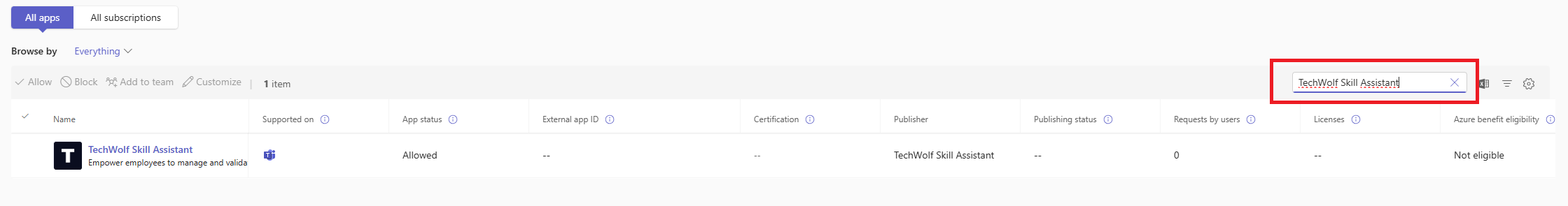
Go to your Teams admin page
Go to your Teams admin page.
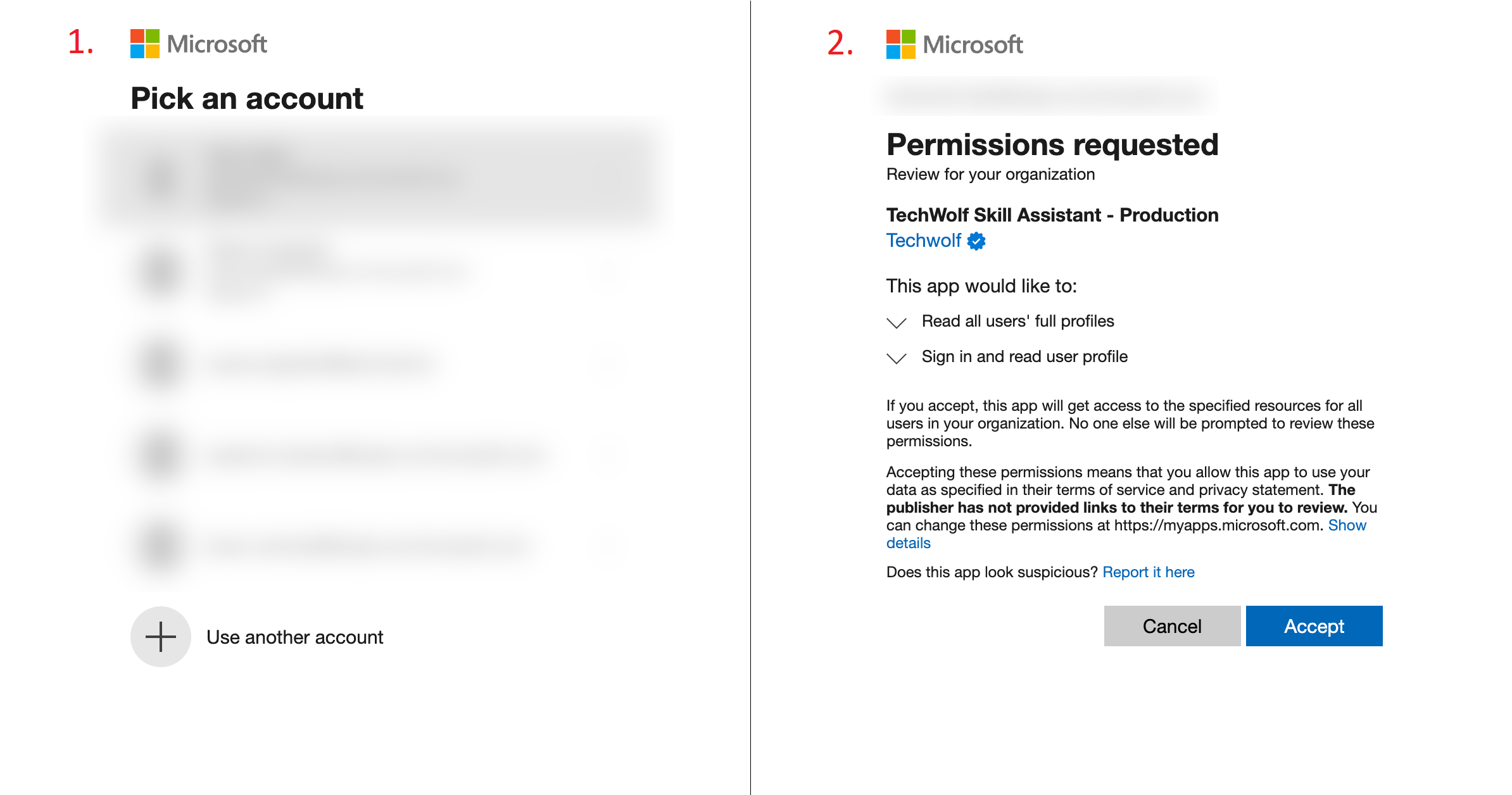
Grant permissions
Grant the app the required permissions. Do so by pressing Grant admin consent (2). This will open a pop up.
More information about the required permissions can be found in the Required permissions of the Skill Assistant application section.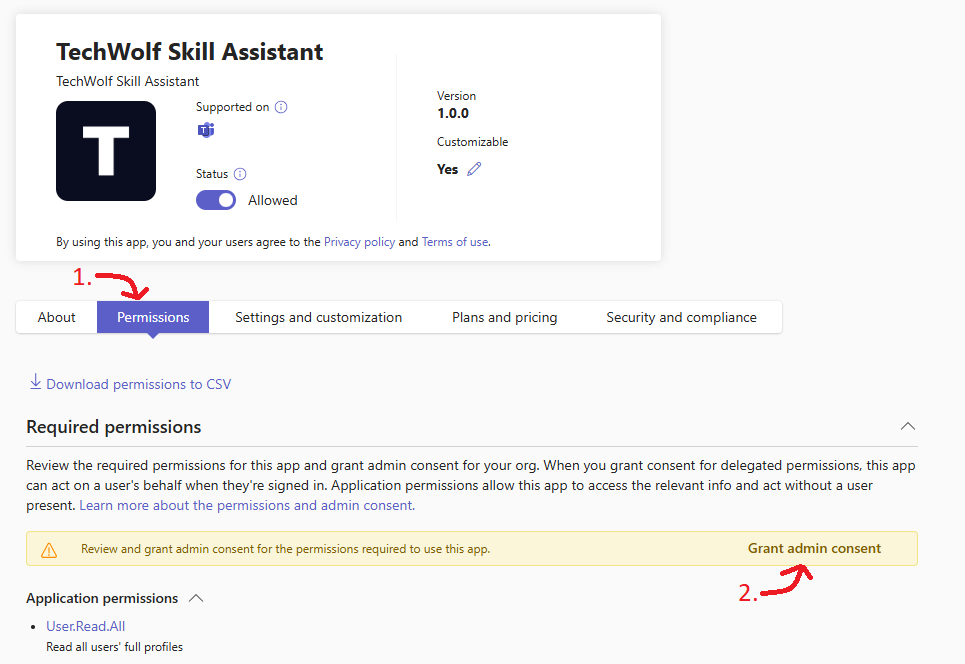

Installing the Skill Assistant for users
Depending on your organisation’s workflow to install apps for employees, you should now install the Skill Assistant for your employees. We recommend the following workflow:Setup user groups
The easiest way to install the app for a subset of users is to create a group in
Azure AD and assign the app to that group. This way, you can easily manage who
has access to the app. To create a group, follow the
Microsoft guide on creating a group.
Setup installation
We recommend to use the app centric management functionality if possible.If you are using app centric functionality, then follow these steps to install the app.If you are not using app centric functionality, then follow these steps to install the app.
Force install using Graph API
If the app is not installed for all users, you can force the installation for
the remaining users using the Microsoft Graph API by following
these steps.
Install the app using App Centric Management
If you are using app centric management for app availability, you can install the app for the group of users by following the following steps.Make app available for users
Make the app available for the group of users by following this guide
from
Microsoft.
Install the app for users
If you are using app centric management for installation, you can
install the app for the group of users by following this guide from
Microsoft.If you are not using app centric management for installation, you can use Setup Policies to install the app for the group of users.
Follow these steps to install the app using Setup Policies.
Install the app without App Centric Management
We recommend to use app centric management for installation if possible.
Install the app using setup policies
You can install the app for a group of users using setup policies. Follow these steps to install the app using Setup Policies.
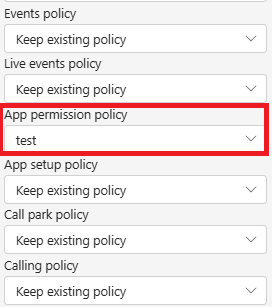
Update permission policy
We recommend to adjust the global permission policy to allow the TechWolf Skill Assistant app.If modifying the global policy is not desired, you can create a new permission policy by following this guide
and assign it to the group by following these steps.
Install the app using Setup Policies
Follow this guide from Microsoft to install the app using Setup Policies. Make sure to apply the setup policy to the group of users by following this section from the Microsoft guide.Assigning the permission policy to a group
This section describes how to assign the permission policy to a group of users.This section is only relevant when you do not have the app centric
management functionality and have created a new permission policy.
These steps require a setup policy to be applied to the group first.
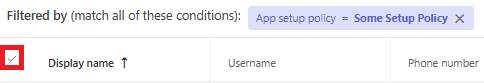
Filter on setup policy
Select the setup policy as filter and the created setup policy as filter value.Click on Apply to apply the filter.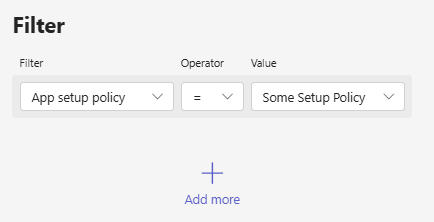

Force installing the app using the Microsoft Graph API
If the app is not installed for all users, you can force the installation for the remaining users using the Microsoft Graph API.Create file with Azure IDs
Create a text file containing all Azure IDs (Object IDs) of the people for which the app
needs to be installed. This file is structured as a list of the Azure IDs,
separated by newlines.
Download the script
We created a template script that you can use to force install the app.
Download the script
Create a new service principal
Create a new service principal in Azure AD to run the script. Follow the
Microsoft guide on creating a service principal.
Create a client secret
A client secret is needed to run the script.In the newly created service principal, select 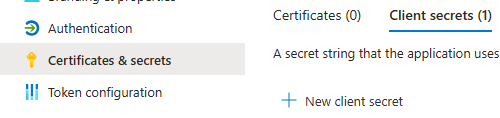
Certificates & secrets.Select Client secrets, and then select New client secret and click Add.You will need this secret later to run the script.
Add the permission
The script requires the 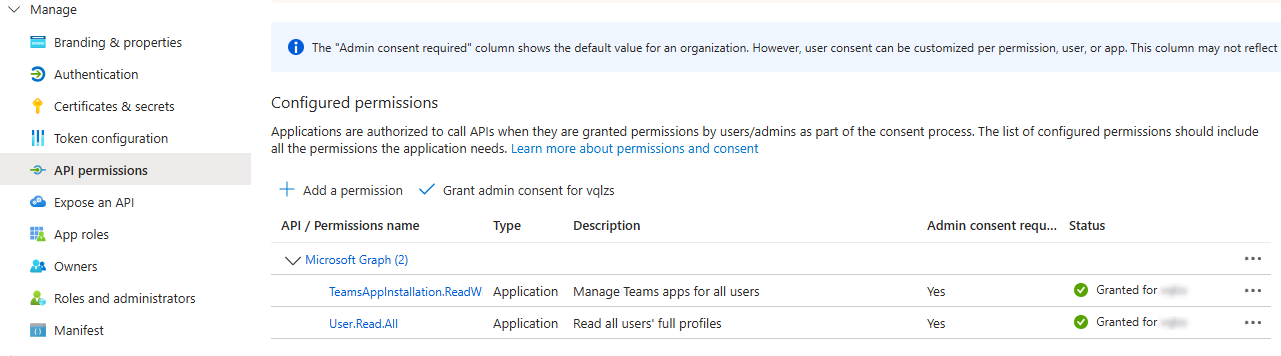
TeamsAppInstallation.ReadWriteForUser.All and User.Read.All permissions.In the service principal, select API permissions.Click on Add a permission and select Microsoft Graph.Select Application permissions and search for
TeamsAppInstallation.ReadWriteForUser.All and select it.Search User.Read.All and select it too.Click on Add permissions to add the permission.Select the added permissions and click Grant admin consent.
Fill in the variables
Fill in the variables in the script:
$FilePath: the path to the previously created file (from Step 1) containing the Azure IDs$ApplicationID: The Application Client ID of the newly created service principal (from step 3)$ClientSecret: The Application Client Secret of the newly created service principal (from step 4)$TenantID: The tenant ID of your Teams instance
Run the script in Powershell
Run the script in Powershell.In Azure Portal, click in the top right on the

Cloud Shell icon.
Manage files and upload the file with Azure IDs and
the filled in script. Run the script by typing ./script.ps1.